Compare pricing, features, and migration paths for top network access control alternatives to Cisco ISE.
"We have 50,000 users and the licensing alone is an enormous cost."
This is the conversation starter we hear regularly from IT directors evaluating their network access control investments. The decision to deploy Cisco ISE increasingly hinges on whether the premium pricing justifies the capabilities - or whether viable alternatives deliver comparable functionality at a fraction of the cost.
Cisco ISE (Identity Services Engine) maintains strong visibility in enterprise procurement discussions.
FreeRADIUS is the
world's most widely deployed RADIUS server, supporting over 100s of
millions of daily users - more than all commercial alternatives
combined.
ISE's licensing model, vendor lock-in characteristics, and operational complexity have driven organisations to re-evaluate Cisco’s offering. The shift from perpetual to subscription licensing particularly frustrated long-time ISE customers who now face recurring annual costs that never end.
This comprehensive guide examines the leading Cisco ISE alternatives available in 2026, breaking down real-world pricing, feature comparisons, and practical migration strategies. Whether you're evaluating ISE for the first time or reconsidering an existing deployment, understanding the complete landscape helps make informed infrastructure decisions.
Quick navigation
Several specific factors trigger organisations to evaluate ISE alternatives:
Subscription licensing costs. ISE subscriptions often range from $15–45 per user annually depending on licensing tier. A 10,000-user deployment costs $220,000–300,000 annually indefinitely. Over five years: $1.1-1.5 million versus the $650,000–750,000 under previous perpetual licensing.
Vendor lock-in. While ISE does implement the standards, it works optimally with Cisco equipment, creating pressure to standardise infrastructure on a single vendor. This reduces negotiating leverage and limits strategic flexibility.
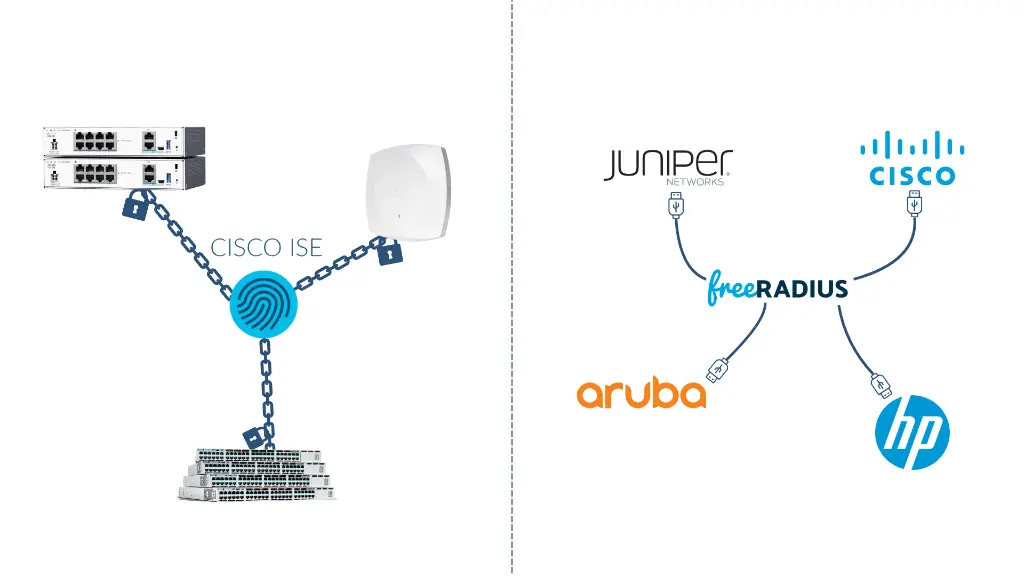
Vendor lock-in with Cisco ISE (left) pressures organisations to standardise on Cisco equipment, while vendor-neutral FreeRADIUS (right) enables best-of-breed equipment selection from any manufacturer.
Support quality disconnect. Despite paying six figures annually, many organisations report long support times, with bug fixes taking another six to 12 months. When you’re a small customer to a large company, your needs are a low priority to them.
Operational complexity. ISE requires dedicated staff, with organisations typically needing 1–5 FTE depending on deployment size. Two full-time administrators represent $780,000–1,200,000 in staffing expenses over five years - often exceeding the software costs themselves.
Understanding these options helps organisations match solutions to their specific requirements rather than defaulting to vendor recommendations or procurement inertia.
Evaluation framework
When comparing alternatives, four factors matter most:
Cost structure. Does the solution charge per-user licensing that scales infinitely with organisational growth, include authentication as part of broader infrastructure licensing, or eliminate licensing fees entirely? Total cost of ownership extends beyond software to encompass support contracts, implementation services, training, and ongoing operational overhead.
Vendor neutrality. Does the solution work equally well with network equipment from any manufacturer, or does it optimise for a specific vendor's ecosystem? Vendor lock-in affects not just immediate purchasing decisions but long-term strategic flexibility and equipment negotiating leverage.
Technical flexibility. Can the solution integrate with existing databases, identity sources, and infrastructure, or does it dictate architectural decisions? The difference between adapting solutions to your environment versus adapting your environment to solutions represents substantial hidden costs.
Operational model. Does the solution require dedicated staff for routine maintenance and policy management, or can commercial support handle troubleshooting while internal teams focus on business-specific requirements? Staffing represents the largest component of authentication infrastructure costs for most organisations.
These factors interact differently based on organisational size, existing infrastructure investments, technical capabilities, and strategic priorities. A 5,000-user organisation heavily invested in Microsoft infrastructure evaluates alternatives differently than a 50,000-user telecommunications provider running mixed-vendor networks.
FreeRADIUS with commercial 24/7 support
What it is: The world's most widely deployed RADIUS server - an open-source implementation supporting 100s of millions of daily users across telecommunications providers, universities, and Fortune 50 enterprises. FreeRADIUS powers more network connections than all commercial alternatives combined. We have multiple customers who run billions of packets a month through FreeRADIUS!
Best for: Organisations seeking vendor neutrality, maximum flexibility, and freedom from per-user licensing costs that scale infinitely with growth.
Cost positioning: Zero software licensing. Organisations invest in implementation expertise, operational tooling, and commercial support when needed. InkBridge Networks provides commercial support packages with defined service levels. No matter what the support level, we come in lower than comparable commercial products. In addition, because FreeRADIUS is more efficient, it also has lower hardware costs.
The combination of lowering these two costs means that either you can save money by switching to FreeRADIUS, or you can get significantly higher capacity for the same cost as ISE.
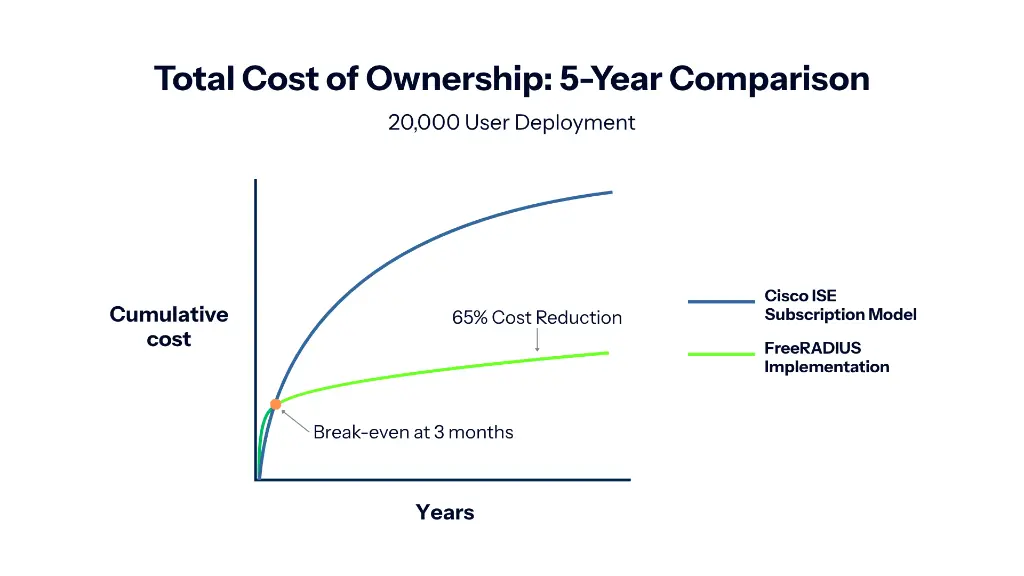
Total cost of ownership comparison over 10 years. FreeRADIUS reaches break-even within 3 months and delivers cumulative savings exceeding $2 million by year five for a typical 20,000-user deployment.
Key strengths:
Dramatic cost reduction with equivalent core capabilities. Cisco recommends a 64-core system with 192GB of RAM for a “medium” ISE deployment. We have never built a FreeRADIUS system with that many CPUs! Instead, we rely on using many smaller systems, where the price/performance ratio is much more favourable. As a result, organisations replacing Cisco ISE with FreeRADIUS implementations typically reduce authentication infrastructure costs by 60–80% while maintaining or improving fundamental AAA capabilities.
Complete vendor neutrality. FreeRADIUS authenticates users identically well, regardless of whether network equipment comes from Cisco, Aruba, Juniper, Extreme Networks, or any standards-compliant vendor. This neutrality provides freedom in equipment purchasing, flexibility for technology evolution, and risk mitigation through avoiding single-vendor dependencies. The vendor neutrality extends to databases - FreeRADIUS works with MySQL, PostgreSQL, Oracle, Microsoft SQL Server, LDAP directories, Redis, or custom integrations.
Proven massive scale. Multiple national telecommunications providers authenticate 10–20 million subscribers on FreeRADIUS infrastructure. Fortune 50 corporations authenticate every wired and wireless connection across hundreds of global locations through FreeRADIUS implementations. Large equipment vendors - including Cisco - test their network devices for FreeRADIUS compatibility before releasing products.
Flexible architecture and integration. FreeRADIUS integrates with any identity source (Active Directory, Azure AD, OAuth providers, certificate authorities), logging destination (syslog servers, SIEM platforms, custom analytics), and policy data source (IP address databases, threat intelligence feeds, custom business logic). The architecture adapts to existing infrastructure rather than forcing infrastructure changes.
Complete protocol flexibility. FreeRADIUS supports modern security standards including RadSec (RADIUS over TLS), RADIUS 1.1 protocol enhancements, and all current EAP methods. Since we write many of the standards, protocol updates appear in FreeRADIUS first, then later in commercial implementations.
(Read Is RADIUS secure? for more detail about how the protocol meets ongoing security standards.)
Customisation without limits. Working with open-source software, organisations can modify anything or hire expertise for custom requirements. Policy engines can incorporate external data sources and conditional processing that GUI-based commercial systems cannot easily express.
Limitations:
No graphical user interface included. FreeRADIUS uses configuration files rather than point-and-click interfaces. This requires greater technical understanding but provides more power and flexibility than GUI-based systems. Third-party management tools exist for organisations preferring graphical interfaces.
The reality is that most organisations don’t need a GUI. Our experience has been that the most common use case for a GUI is monitoring, followed by user management. We provide a monitoring GUI that displays system status.
All user management can be done via a database (“our API is SQL”). In addition, a GUI provides a false sense of capabilities, because policy management cannot be done via a GUI. Complex policies require programming, which can’t be done via a “point and click” GUI.
The result is that we have enough of a GUI for common use cases, and the uncommon ones cannot be done easily with a GUI anyways.
Initial learning curve. Teams accustomed to commercial platforms with extensive GUIs may face an adjustment period when adopting configuration-file-based management. Commercial support and training from InkBridge Networks accelerates this transition.
Again, the reality is that policies don’t change that often. Once a policy is set, its lifetime is typically months to years. Customers needing policy changes can always ask for help from support, who will recommend the most efficient way to reach the goal.
When to consider:
Any organisation seeking to escape vendor lock-in. FreeRADIUS provides the only authentication infrastructure that doesn't pressure you toward a specific equipment vendor's ecosystem.
Deployments where per-user licensing would exceed implementation costs. Organisations with 5,000+ users typically save substantial money with FreeRADIUS even accounting for commercial implementation services and support.
Requirements for database flexibility. When performance, compliance, or existing expertise dictates specific database choices, FreeRADIUS adapts to your requirements rather than forcing architectural decisions.
Massive scale requirements. Telecommunications providers and very large enterprises often find FreeRADIUS handles scale more efficiently than commercial alternatives designed around appliance models.
Need for customisation beyond vendor roadmaps. Organisations with unique requirements that commercial vendors won't prioritise can modify FreeRADIUS or hire expertise for custom development.
InkBridge Networks commercial support
The core team that created and maintains FreeRADIUS provides commercial implementation services, support packages, and expert consultation through InkBridge Networks. This combines open-source flexibility with enterprise-grade support, guaranteed response times, expert troubleshooting, and proactive monitoring - without multi-year subscription commitments or per-user licensing fees.
Support packages include defined service levels, direct access to FreeRADIUS experts who wrote the software, assistance with policy design and troubleshooting, and proactive monitoring. Organisations receive enterprise-level support without the multi-month response times some experience with large vendor support contracts.
Microsoft NPS (Network Policy Server)
What it is: Microsoft's RADIUS server implementation, bundled with Windows Server at no additional licensing cost beyond Windows Server itself.
Best for: Small organisations with simple authentication requirements, existing Windows Server infrastructure, and no plans to diversify beyond the Microsoft ecosystem.
Cost positioning: Included with Windows Server licensing - no separate authentication software costs, though Windows Server licensing itself represents substantial investment. A 10,000-user deployment requires Windows Server infrastructure but adds no incremental authentication licensing costs.
Key strengths:
No additional licensing fees. Beyond Windows Server costs, NPS adds no authentication-specific licensing. For organisations already running Windows Server infrastructure, this represents real savings compared to per-user commercial NAC platforms.
Active Directory integration. NPS integrates directly with Active Directory for authentication, authorisation, and user management. Organisations using Active Directory as their primary identity source find this integration straightforward.
Familiar management interface. Windows administrators understand NPS's management console and configuration approach without learning new management paradigms. The learning curve is minimal for teams already managing Windows infrastructure.
Works adequately for basic scenarios. Simple network access control requirements - authenticating users against Active Directory for Wi-Fi or VPN access - work reasonably well with NPS.
Limitations:
Locked to Active Directory exclusively. NPS cannot use other databases or identity sources. This architectural constraint forces all authentication through Active Directory regardless of whether that makes sense for specific use cases.
Relies on deprecated MS-CHAP protocol. NPS's tight Active Directory integration depends on MS-CHAP, an authentication protocol with known security vulnerabilities. Modern authentication methods work poorly or not at all with NPS's architecture.
No device profiling capabilities. NPS cannot identify device types, operating systems, or characteristics beyond basic authentication. Organisations wanting to differentiate policies based on device characteristics need different solutions.
Minimal development investment from Microsoft. The product has received nothing more than security fixes for 20 years. Feature development essentially stopped decades ago. New networking requirements and authentication methods appear in other solutions long before - if ever - appearing in NPS.
For example, NPS does not currently implement RadSec and is likely to never implement it. Any other new standards (e.g. Protocol-Error) are also unlikely to ever be implemented in NPS.
Limited advanced features. Guest access requires separate products. Device compliance checking needs third-party tools. Policy enforcement beyond basic VLAN assignment requires additional infrastructure.
Constrained by Windows Server performance. NPS scales to Windows Server's limitations rather than authentication workload requirements. Very large deployments need many servers to handle load that other solutions manage on fewer systems.
When to consider:
Small organisations with simple requirements. Organisations under 5,000 users with straightforward authentication needs and existing Windows Server infrastructure may find NPS adequate.
Windows-centric environments. Organisations heavily invested in the Microsoft ecosystem with limited non-Windows systems may accept NPS's limitations because Active Directory integration simplifies operations elsewhere.
Very limited authentication budget. Budget constraints sometimes force choosing between no authentication infrastructure and NPS. NPS wins that comparison.
When to avoid:
Need for modern authentication protocols. If security requirements include current authentication methods, NPS's Active Directory dependencies create unacceptable limitations.
Advanced device profiling requirements. Organisations wanting comprehensive device identification and policy differentiation need dedicated NAC platforms.
Comprehensive guest access needs. NPS's lack of guest access features makes it unsuitable for environments where visitor connectivity matters.
Mixed-vendor network equipment. While NPS technically works with any RADIUS-compliant equipment, the Windows-centric approach fits poorly with diverse network infrastructure.
Complex access policy requirements. Sophisticated policies based on multiple factors exceed NPS's capabilities.
Aruba ClearPass
What it is: HPE Aruba's commercial network access control platform, competing directly with Cisco ISE as a full-featured NAC solution. ClearPass is based on a 15-year-old version of FreeRADIUS, with many customisations.
Best for: Organisations using Aruba wireless infrastructure or seeking feature-rich commercial NAC with less vendor lock-in than Cisco ISE.
Cost positioning: Per-user or per-device licensing similar to Cisco ISE but typically 20–30% less expensive. A 10,000-user deployment costs approximately $220,000–350,000 annually including licensing and support - less than ISE but substantially more than open-source alternatives.
Key strengths:
Comprehensive feature set. ClearPass provides guest access portals, device profiling, posture assessment, automated provisioning, and sophisticated policy engines. Feature parity with Cisco ISE makes it a direct alternative for organisations wanting commercial NAC platforms.
Better multi-vendor support than ISE. While ClearPass optimises for Aruba equipment, it works reasonably well with other vendors' network infrastructure. Organisations aren't as locked into single-vendor ecosystems as with Cisco ISE.
Easier deployment than Cisco ISE. ClearPass's reputation for simpler configuration and management compared to ISE attracts organisations wanting commercial NAC without ISE's complexity.
Strong wireless integration. For organisations using Aruba wireless controllers and access points, ClearPass provides deep integration that simplifies policy enforcement and troubleshooting.
Limitations:
Still uses per-user licensing that scales with growth. Like Cisco ISE, ClearPass charges based on user count. Organisational growth increases authentication costs indefinitely.
Creates Aruba ecosystem pressure. While less severe than Cisco's lock-in, ClearPass works best with Aruba equipment. This influences purchasing decisions and reduces equipment vendor negotiating leverage.
Requires dedicated staff for management. Complex policy environments, guest access portal maintenance, and troubleshooting require ongoing staff attention similar to Cisco ISE.
Subscription costs continue indefinitely. Like ISE, ClearPass has moved to subscription licensing. The authentication infrastructure you depend on requires annual payments that never convert to owned assets.
When to consider:
Using Aruba wireless infrastructure. Organisations with Aruba controllers and access points gain operational advantages from adding ClearPass.
Need commercial NAC with less lock-in than ISE. ClearPass provides middle ground between Cisco's ecosystem lock-in and vendor-neutral open-source solutions.
Want comprehensive features with easier deployment than ISE. Organisations needing guest portals, device profiling, and sophisticated policies but finding ISE too complex may prefer ClearPass.
When to avoid:
Per-user licensing costs exceed budget. ClearPass costs less than ISE but still represents substantial ongoing expense. Organisations with large user bases may find open-source alternatives more economical.
Want vendor neutrality. While better than ISE, ClearPass still creates vendor ecosystem pressures. Truly vendor-neutral infrastructure requires different approaches.
Primarily using non-Aruba equipment. ClearPass's advantages diminish when most network equipment comes from other vendors.
These primary decision factors determine which alternative is most appropriate for your organisation.
Budget and economics. Calculate total five-year costs including licensing or subscriptions, commercial support, infrastructure, implementation services, training, and dedicated staff. Organisations with 10,000+ users typically save 60–80% by choosing FreeRADIUS over commercial alternatives. Smaller deployments may prioritise ease of implementation over long-term cost savings.
Vendor neutrality requirements. Do you want freedom to select network equipment based on merit and price, or are you comfortable standardising on a single vendor's ecosystem? Organisations seeking vendor independence require vendor-neutral solutions. Those already committed to specific ecosystems may accept the limitations.
Technical capabilities. Honest assessment of internal expertise matters. Teams with authentication protocol expertise can manage any solution. Organisations lacking specialised skills may prefer commercial platforms with comprehensive vendor support or engage implementation partners like InkBridge Networks for FreeRADIUS deployments.
Vendor consolidation strategy. Some organisations discover they can simplify vendor relationships while escaping ecosystem lock-in. For example, InkBridge Networks provides RADIUS authentication alongside DHCP and TACACS+ implementations, addressing multiple network infrastructure needs through excellent engineering rather than forcing organisations into a single vendor's complete product portfolio.
This consolidation approach reduces integration complexity and support finger-pointing without creating the vendor lock-in that commercial NAC platforms impose. Customer feedback consistently mentions the desire to simplify vendor relationships - purchasing from too many vendors creates operational nightmares, but consolidating with vendors like Cisco or Aruba, which are focused on ecosystem lock-in, creates strategic risks.
Scale and complexity. Simple environments with basic authentication requirements suit any alternative. Large-scale deployments (50,000+ users), geographically distributed infrastructures, or complex policy requirements need proven scalability. FreeRADIUS handles massive scale most economically, having been deployed by telecommunications providers with 10-20 million users.
Feature requirements. Do you need built-in guest access portals, advanced device profiling, and graphical policy interfaces? Commercial NAC platforms include these features. FreeRADIUS provides core authentication excellently but requires third-party integration or custom development for advanced features.
Matching Cisco ISE alternatives to situations
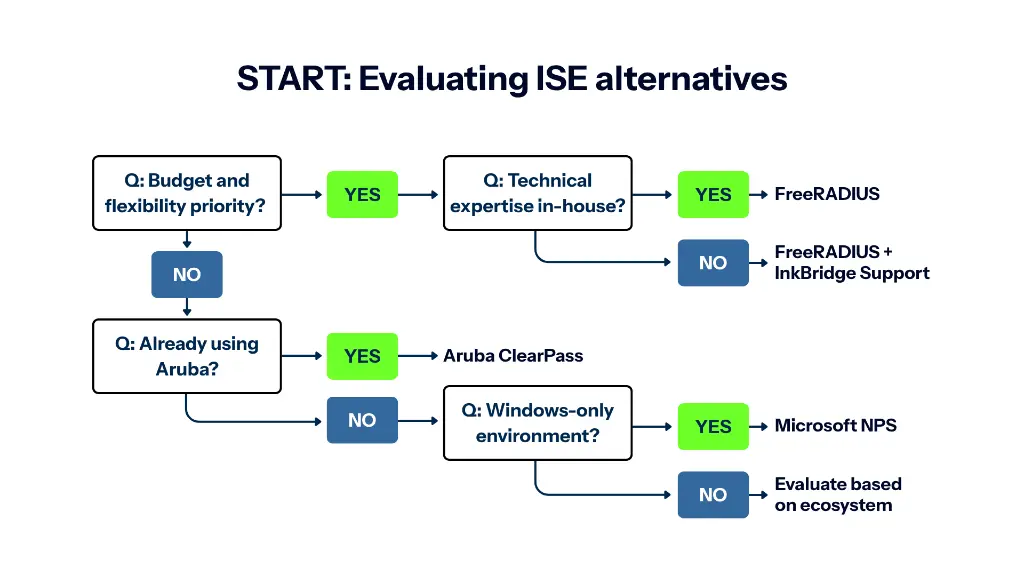
Decision framework for selecting the right Cisco ISE alternative based on your organisation's priorities and infrastructure.
Choose FreeRADIUS when: Cost sensitivity matters, vendor neutrality is a strategic priority, deployment exceeds 10,000 users, you have technical expertise or can engage commercial implementation partners, or database flexibility is required.
Choose Microsoft NPS when: Your environment is predominantly Windows-centric, authentication requirements are simple, budget is severely constrained, and Active Directory meets all identity management needs.
Choose commercial NAC platforms when: You need comprehensive built-in features, prefer graphical management interfaces, want single-vendor support, can absorb ongoing subscription costs, and already use that vendor's ecosystem.
No universal best alternative exists - the right choice depends on your priorities, capabilities, and infrastructure realities.
What are the best alternatives to Cisco ISE?
The leading Cisco ISE alternatives in 2026 are:
- FreeRADIUS: Open-source RADIUS server supporting 100+ million daily users. Zero licensing costs, complete vendor neutrality, 60–80% cost savings compared to ISE. Best for: organisations seeking vendor independence and lower TCO.
- Aruba ClearPass: Commercial NAC platform with comprehensive features. Easier deployment than ISE. Best for: Aruba infrastructure environments.
- Microsoft NPS: Included with Windows Server at no additional cost. Limited features, Active Directory only. Best for: small Windows-centric organisations with simple authentication needs.
- Fortinet FortiNAC: Integrated security NAC. Best for: existing Fortinet security ecosystem deployments.
FreeRADIUS offers the lowest total cost of ownership while maintaining enterprise-grade capabilities. Commercial alternatives provide easier deployment with ongoing subscription costs.
Can FreeRADIUS replace all Cisco ISE features?
FreeRADIUS provides core AAA functionality equivalent to Cisco ISE for 802.1X authentication, VPN access, and policy enforcement. It includes all EAP methods, flexible policy engines, comprehensive logging, and vendor-neutral operation. FreeRADIUS requires add-ons for guest portals and graphical policy interfaces, and doesn't support Cisco-proprietary features like TrustSec. For most organisations, FreeRADIUS plus selective add-ons provide needed functionality at a fraction of ISE's cost.
Does FreeRADIUS work with Cisco network equipment?
Yes. Both Cisco ISE and FreeRADIUS implement standard RADIUS protocols. Your existing Cisco switches, wireless controllers, and firewalls authenticate via FreeRADIUS identically to ISE. No equipment changes needed - migration requires only updating RADIUS server IP addresses. Cisco actually tests their equipment for FreeRADIUS compatibility before releases.
How long it take to migrate to FreeRADIUS?
Typical migrations span one to six months, depending on the complexity of the system. The migration is split across four phases: assessment and planning, pilot deployment , phased rollout, and complete cutover. The timeline varies based on deployment complexity and organisational change management. The phased approach maintains the current system as a fallback throughout the transition.
What support options exist for FreeRADIUS?
Multiple options suit different needs: free community support through active mailing lists and forums with rapid response; commercial support from InkBridge Networks providing enterprise-grade SLAs, guaranteed response times, and expert troubleshooting; and implementation partner support for deployment and knowledge transfer. Unlike commercial vendors where mid-tier customers report 3–6 month response times, the FreeRADIUS community often fixes critical bugs within hours.
Do I need to replace network equipment when migrating?
No. RADIUS is a standard protocol - your existing Cisco, Aruba, Juniper, or other standards-compliant equipment works with any RADIUS server. Migration requires only configuration changes: update server IP addresses and shared secrets. This vendor neutrality eliminates equipment lock-in and enables best-of-breed infrastructure decisions.
Need help?
If you're evaluating Cisco ISE alternatives and want to understand how a vendor-neutral RADIUS implementation like FreeRADIUS could work for your organisation, we can help. InkBridge Networks provides expert consultation, implementation support, and commercial services for organisations seeking flexible, cost-effective AAA solutions.
Get a quote for support and implementation services tailored to your specific infrastructure requirements and security needs.
Related Articles

Is RADIUS secure?
“Is RADIUS secure?” is one of the most common questions network administrators ask when evaluating authentication infrastructure. In fact, RADIUS is more secure today than it has ever been, thanks to systematic security-by-design improvements at the standards level.

Steel-Belted RADIUS Server End-of-Life: What You Need to Know Now
If you're still running Steel-Belted RADIUS server (SBR), you're operating on borrowed time. SBR Enterprise and Global Enterprise reached end-of-life on December 31, 2020. The Carrier Edition's End of Engineering came on February 28, 2023, followed by End of Support on September 30, 2023.